Why Cloud Security Compliance Matters for Saudi Financial Institutions
The banking sector in Saudi Arabia faces unprecedented regulatory scrutiny as cloud security compliance becomes mandatory for financial operations. With Vision 2030 accelerating digital adoption and the Saudi Central Bank (SAMA) enforcing strict regulations, banks and financial services providers must master cloud security compliance requirements while maintaining operational excellence.
The recent surge in cloud adoption among Saudi financial institutions, with over 70% planning to migrate critical workloads to the cloud by 2025, demands immediate attention to cloud security compliance frameworks. This article addresses the specific questions Saudi financial leaders need answered about securing their cloud infrastructure.
Understanding Cloud Security Compliance: The Foundation
What is Cloud Security Compliance?
Cloud security compliance means adhering to regulatory standards, industry requirements, and internal policies when storing, processing, and managing data in cloud environments. Saudi financial institutions must align with SAMA’s Cybersecurity Framework, international standards including ISO 27001, and regional data residency mandates.
This requirement covers multiple security controls, from data encryption and access management to incident response and business continuity. Saudi banks must verify their cloud security compliance strategies address local regulations alongside international standards, particularly for cross-border transactions.
The 4 Main Cloud Services and Their Compliance Implications
Saudi financial institutions must understand four primary cloud service models when planning cloud security compliance strategies:
- Infrastructure as a Service (IaaS): Provides virtualized computing resources, requiring institutions to manage operating systems and applications while ensuring compliance at the infrastructure level.
- Platform as a Service (PaaS): Offers development and deployment environments where cloud security compliance responsibilities are shared between the provider and the financial institution.
- Software as a Service (SaaS): Delivers complete applications where providers handle most compliance aspects, though data governance remains the institution’s responsibility.
- Function as a Service (FaaS): Enables serverless computing, presenting unique cloud security compliance challenges in terms of data flow and processing visibility.
For more insights on digital transformation in Saudi businesses, visit Alnafitha’s guid.
The 6 Pillars of Cloud Security Compliance
Saudi financial institutions building cloud security compliance programs must address six foundational pillars:
1. Identity and Access Management (IAM)
Multi-factor authentication, privileged access management, and regular access reviews meet SAMA requirements for cloud security compliance. Saudi financial institutions implement these controls to prevent unauthorized access.
2. Data Protection and Privacy
Encryption at rest and in transit is mandatory for cloud security compliance in the financial sector. Institutions must ensure data residency within Saudi Arabia when required and implement data loss prevention (DLP) solutions.
3. Infrastructure Security
Network segmentation, firewalls, and intrusion detection systems are essential components of cloud security compliance frameworks. Saudi banks must maintain visibility across hybrid and multi-cloud environments.
4. Application Security
Secure coding practices, regular vulnerability assessments, and application-level encryption ensure cloud security compliance at the software layer. This includes implementing secure DevOps practices and automated security testing.
5. Incident Response and Recovery
Documented incident response plans support cloud security compliance requirements. Financial institutions establish 24/7 monitoring, incident escalation procedures, and scheduled disaster recovery testing.
6. Governance and Risk Management
Regular audits, documented policies, and continuous monitoring maintain cloud security compliance standards. This includes documentation for regulatory reviews and risk assessment frameworks.
Need assistance with compliance implementation? Schedule a consultation with our sales team to discuss your requirements.
The 4 Pillars of AWS Cloud Security for Saudi Banks
Amazon Web Services provides specific cloud security compliance features widely adopted by Saudi financial institutions:
1. Data Protection
AWS offers encryption services, key management, and data residency controls required for cloud security compliance in Saudi Arabia’s financial sector.
2. Infrastructure Protection
Virtual private clouds, network access control lists, and security groups support cloud security compliance at the infrastructure level.
3. Application Protection
AWS Web Application Firewall and Shield provide protection against common threats, supporting cloud security compliance requirements.
4. Identity and Compliance
AWS Identity and Access Management (IAM) and AWS Organizations help financial institutions maintain cloud security compliance through centralized control and governance.
For detailed AWS compliance information, refer to AWS Compliance Programs.
The 4 Types of Cloud Security for Financial Services
1. Public Cloud Security
Public cloud deployments demand specific cloud security compliance measures, including data encryption, network isolation, and continuous monitoring to protect financial data.
2. Private Cloud Security
Many Saudi banks opt for private clouds to maintain greater control over cloud security compliance, especially for core banking systems and sensitive customer data.
3. Hybrid Cloud Security
Hybrid environments create specific cloud security compliance requirements, demanding consistent security policies across on-premises and cloud infrastructure.
4. Multi-Cloud Security
When institutions adopt multiple cloud providers, maintaining cloud security compliance across platforms requires unified security management tools and processes.
Common Cloud Security Tools for Saudi Financial Institutions
Security Tools for Cloud Compliance
- Cloud Access Security Brokers (CASBs): Provide visibility and control over data movement, required for cloud security compliance in multi-cloud environments.
- Cloud Workload Protection Platforms (CWPPs): Secure workloads across different cloud environments, maintaining consistent cloud security compliance.
- Cloud Security Posture Management (CSPM): Monitor and remediate misconfigurations that could affect cloud security compliance.
- Cloud Infrastructure Entitlement Management (CIEM): Manage permissions and access rights across cloud platforms, supporting cloud security compliance requirements.
Which Cloud Tool is Best for Cybersecurity?
Saudi financial institutions select tools based on their cloud security compliance requirements. Microsoft Azure Security Center and AWS Security Hub offer security management features aligned with local regulations.
Security platforms including Palo Alto Prisma Cloud and Check Point CloudGuard provide threat protection while supporting cloud security compliance mandates for the Saudi financial sector.
The 4 Areas of Cloud Security Compliance
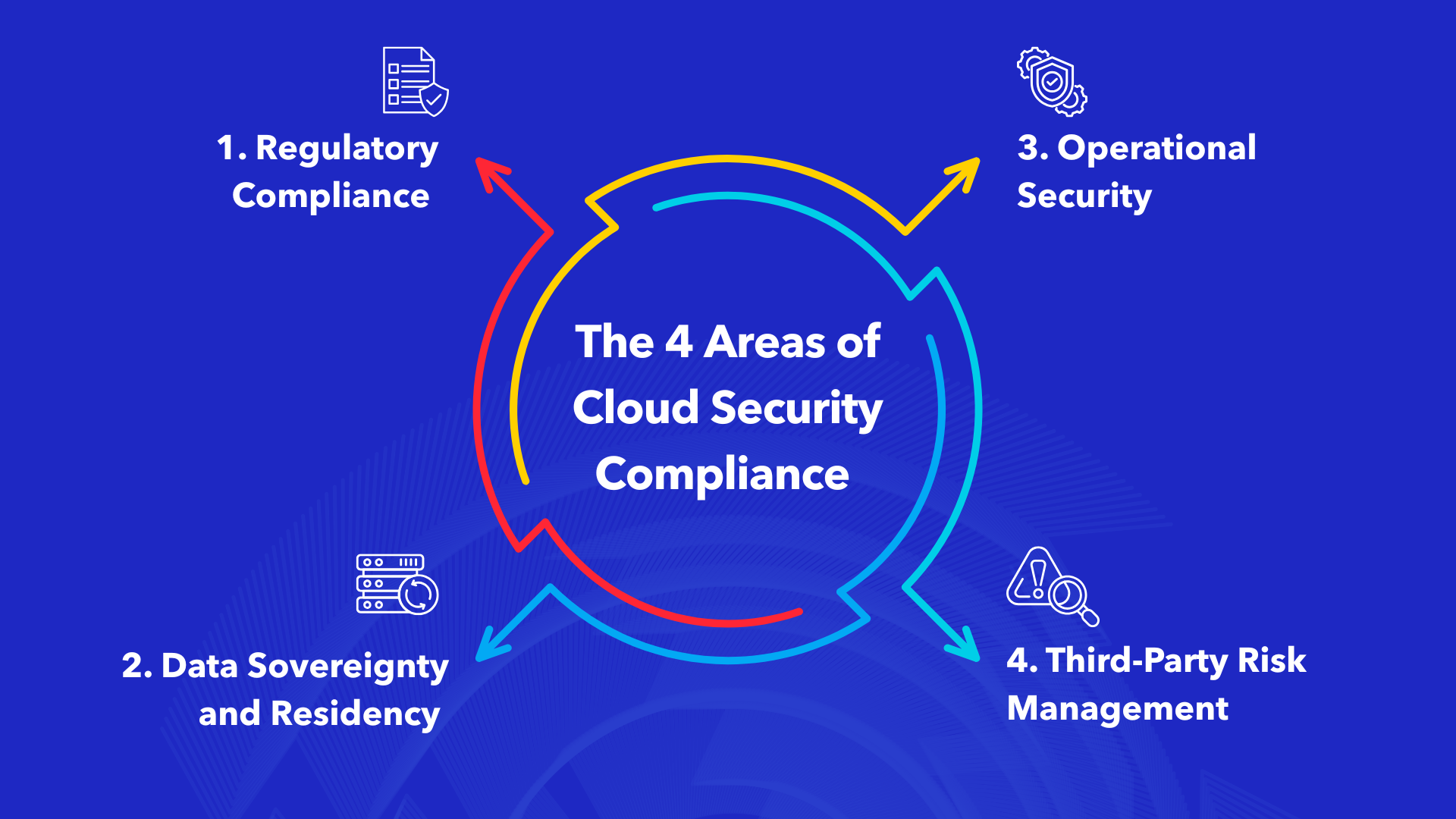
1. Regulatory Compliance
Saudi financial institutions must adhere to SAMA’s Cybersecurity Framework, ensuring cloud security compliance with local banking regulations and international standards like PCI DSS for payment card data.
2. Data Sovereignty and Residency
Maintaining data within Saudi Arabia’s borders is often mandatory for cloud security compliance, requiring careful selection of cloud regions and data centers.
3. Operational Security
Monitoring, logging, and auditing maintain cloud security compliance, with security operations centers (SOCs) managing these activities.
4. Third-Party Risk Management
Vendor assessments and supply chain security support cloud security compliance, particularly when working with international cloud providers.
Best Practices for Cloud Security Compliance in Saudi Financial Institutions
Implementing a Risk-Based Approach
Cloud security compliance strategies should rank risks based on potential impact to the institution and customers:
- Scheduled risk assessments aligned with SAMA guidelines
- Active monitoring of emerging threats
- Adaptive security controls using threat intelligence
- Connection with enterprise risk management frameworks
Building a Security Culture
Achieving cloud security compliance demands organization-wide commitment:
- Executive sponsorship with defined governance structures
- Scheduled training and awareness programs
- Documented roles and responsibilities for cloud security
- Recognition programs for security-conscious behavior
Using Automation for Compliance
Automation improves cloud security compliance through:
- Automated policy enforcement and remediation
- Real-time compliance monitoring and reporting
- Automated incident response workflows
- Security integration in development processes
For more information on digital transformation strategies, explore Alnafitha’s business strategies.
Examples of Cloud Security in Saudi Financial Institutions
Major Saudi Bank Cloud Migration
A prominent Saudi bank achieved cloud security compliance while migrating 60% of applications to the cloud:
- 40% reduction in security incidents
- 50% faster compliance audit completion
- Improved customer data protection
- Strengthened disaster recovery capabilities
Islamic Banking Cloud Implementation
An Islamic financial institution deployed cloud security compliance measures including:
- Sharia-compliant data handling procedures
- Zero-trust security architecture
- Advanced encryption for customer transactions
- Automated compliance reporting for regulators
Future Trends in Cloud Security Compliance
New Technologies and Their Impact
Cloud security compliance will incorporate advancing technologies:
- Machine Learning and Automated Intelligence: Pattern recognition for threat detection supporting cloud security compliance
- Zero Trust Architecture: Verification of every transaction without assumed trust
- Quantum-Resistant Cryptography: Preparation for next-generation encryption requirements
- Blockchain Audit Trails: Unchangeable logs supporting cloud security compliance documentation
Regulatory Changes
Saudi Arabia’s cloud security compliance regulations continue developing:
- Expanded data localization requirements
- Faster incident reporting timelines
- Focus on operational resilience
- Stronger third-party risk management
Key Takeaways for Saudi Financial Leaders
Strategic Recommendations
- Build a Cloud Security Strategy: Connect cloud security compliance programs with business objectives and regulatory requirements
- Invest in Team Development: Develop internal expertise in cloud security compliance through training and certification
- Establish Governance Frameworks: Document policies and procedures for cloud security compliance across cloud deployments
- Deploy Continuous Monitoring: Install tools and processes for real-time cloud security compliance tracking and reporting
- Encourage Industry Collaboration: Partner with regulators, cloud providers, and industry peers to improve cloud security compliance practices
Implementation Steps
- Assess current cloud security compliance maturity levels
- Create a roadmap addressing identified gaps
- Allocate resources for cloud security compliance programs
- Define metrics and KPIs for measuring compliance performance
- Schedule reviews and updates of cloud security compliance strategies
Conclusion: Securing Saudi Arabia’s Financial Future
Cloud security compliance represents both a regulatory requirement and competitive advantage for Saudi financial institutions. By deploying security frameworks, using advanced technologies, and maintaining oversight, banks can embrace cloud transformation while protecting customer assets and data.
Saudi Arabia’s Vision 2030 journey demands that financial institutions prioritize cloud security compliance to position themselves for growth and innovation in the digital economy. Investment in cloud security compliance today delivers returns in operational efficiency, customer trust, and regulatory confidence.
Don’t wait to secure your cloud infrastructure. Contact our sales team today and discover how we can accelerate your compliance journey.
To learn more about global cloud security standards, explore resources from the Cloud Security Alliance.
