Are your current security measures actually protecting your business, or just giving you a false sense of safety? The Saudi Arabian business landscape is rapidly evolving, with Public Investment Fund (PIF)-backed enterprises leading the charge in digital transformation. As these organizations expand their technological infrastructure, implementing robust Zero Trust Security frameworks becomes critical for protecting valuable assets and maintaining operational excellence.
Understanding Modern Security Architecture Principles
The Foundation of Zero Trust Security
Traditional security models relied on perimeter-based defences, assuming everything inside the network was trustworthy. However, modern Zero Trust Security approaches operate on the principle of “never trust, always verify.” This paradigm shift is particularly crucial for PIF-backed enterprises that handle sensitive financial data and strategic national investments.
According to the National Institute of Standards and Technology (NIST), Zero Trust Security eliminates the concept of trusted networks and focuses on continuous verification. The core principle centers around three fundamental pillars:
- Explicit verification: Every access request requires authentication
- Least privilege access: Users receive minimum necessary permissions
- Assume breach: Security systems operate under the assumption that threats already exist
Implementing Zero Trust Architecture in Saudi Organizations
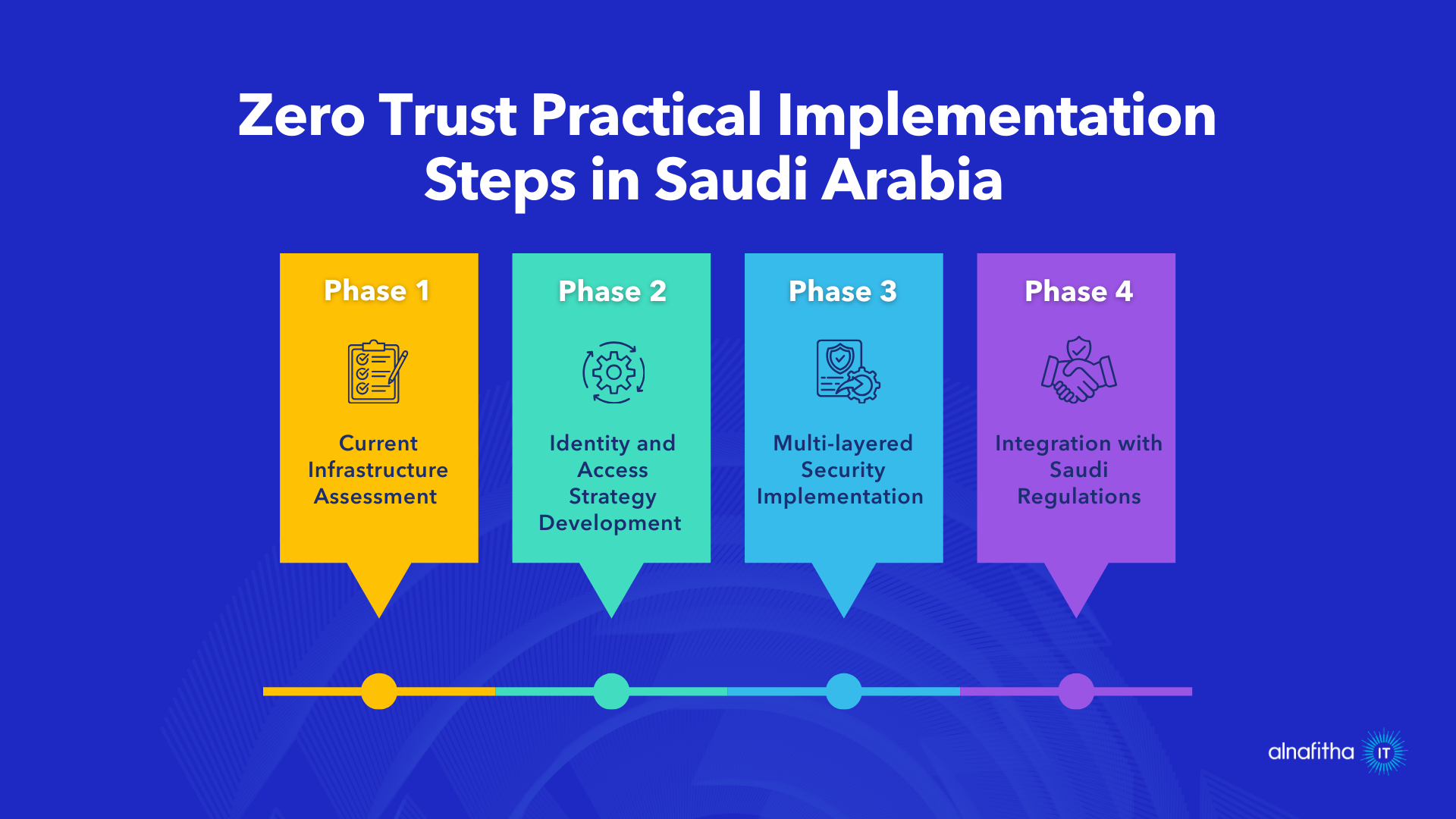
For Saudi enterprises, adopting Zero Trust Security solutions requires understanding local regulatory requirements and business practices. Organizations must balance stringent security measures with operational efficiency, ensuring compliance with Saudi Data and AI Authority (SDAIA) guidelines while maintaining productivity.
Modern security architecture integrates seamlessly with existing enterprise systems, providing complete protection without disrupting daily operations. This approach proves especially valuable for organizations managing multiple business units across different sectors, as outlined in Microsoft’s Zero Trust implementation guide.
Identity and Device Verification: Zero Trust Security Cornerstone
Advanced Authentication Methods for Saudi Enterprises
Zero Trust Security implementations prioritize robust identity verification processes. Multi-factor authentication (MFA) serves as the first line of defense, combining something users know (passwords), something they have (mobile devices), and something they are (biometric data).
According to Gartner’s 2024 Zero Trust survey, 63% of organizations worldwide have implemented Zero Trust strategies, with 95% of decision-makers agreeing that Zero Trust reduces security incidents. For PIF-backed enterprises operating across diverse sectors, identity management becomes increasingly complex. Organizations require solutions that accommodate various user types, from executive leadership to field technicians, each with distinct access requirements and security protocols.
Device Security and Compliance Standards
Every device connecting to enterprise networks undergoes rigorous verification processes. Zero Trust Security frameworks evaluate device health, compliance status, and potential security risks before granting network access. This systematic approach ensures that compromised or non-compliant devices cannot infiltrate organizational systems.
Device verification encompasses several critical components:
- Endpoint detection and response (EDR) capabilities
- Real-time threat assessment and monitoring
- Automated compliance checking and reporting
- Secure device enrolment and management protocols
Modern enterprises leverage cloud-based device management solutions that provide centralized control while accommodating remote work requirements and distributed organizational structures, following ISO 27001 security standards.
Threat Detection and Response: Zero Trust Security Measures
Real-Time Monitoring and Analysis
Zero Trust Security solutions excel in continuous monitoring and threat detection. Advanced artificial intelligence and machine learning algorithms analyse network traffic, user behaviour, and system activities to identify potential security incidents before they escalate.
According to the Cybersecurity and Infrastructure Security Agency (CISA), organizations with mature Zero Trust implementations detect threats 200 times faster than traditional security models. Threat detection systems provide extensive visibility across all network segments, applications, and user activities. This holistic approach enables security teams to respond quickly to emerging threats while minimizing false positives that can overwhelm operational resources.
Incident Response and Recovery Protocols
Effective incident response requires well-defined procedures and automated response capabilities. When security incidents occur, Zero Trust Security systems automatically contain threats, preserve evidence, and initiate recovery procedures to minimize business impact.
Response protocols typically include:
- Immediate threat containment and isolation
- Forensic data collection and preservation
- Stakeholder notification and communication
- Recovery planning and execution
- Post-incident analysis and improvement recommendations
For PIF-backed enterprises, rapid response capabilities prove essential for maintaining stakeholder confidence and regulatory compliance while protecting organizational reputation and financial assets.
Scalability for Large Organizations: Zero Trust Security Demands
Infrastructure Requirements and Planning
Large Saudi enterprises require Zero Trust Security solutions that scale efficiently across multiple locations, business units, and user populations. Cloud-native security platforms provide the flexibility and scalability necessary to accommodate organizational growth while maintaining consistent security policies.
Research from Enterprise Strategy Group (ESG) indicates that organizations implementing Zero Trust solutions achieve a 139% return on investment (ROI) with average savings of $4 million. Additionally, Forrester’s Total Economic Impact study found that Microsoft Zero Trust implementations deliver 92% ROI with 50% reduction in security management time. Scalability considerations include network bandwidth requirements, user capacity planning, and integration with existing enterprise systems. Organizations must evaluate their current infrastructure capabilities and plan for future expansion to ensure seamless security implementation.
Cost-Effective Zero Trust Security Implementation Strategies
Implementing robust Zero Trust Security solutions requires strategic budget allocation and phased deployment approaches. Organizations benefit from starting with critical assets and high-risk user groups before expanding coverage across the entire enterprise.
Cost optimization strategies include leveraging existing security investments, prioritizing high-impact security controls, and selecting vendors that provide flexible licensing and deployment options. Many organizations find that cloud-based solutions offer better cost predictability and reduced infrastructure overhead compared to traditional on-premises alternatives.
Zero Trust Security Integration with Existing Enterprise Systems
Successful Zero Trust Security implementations require seamless integration with existing enterprise applications, identity management systems, and operational workflows. Organizations must evaluate compatibility requirements and plan for necessary system modifications or replacements.
Integration typically involves connecting with active directory services, single sign-on solutions, enterprise resource planning systems, and various business applications. Modern security platforms provide extensive API capabilities and pre-built connectors that simplify integration processes.
Best Practices for Zero Trust Security in Saudi Arabia
Regulatory Compliance and Local Requirements
Saudi organizations must ensure their Zero Trust Security implementations comply with local regulations, including data residency requirements, privacy protection standards, and sector-specific compliance mandates. Understanding these requirements early in the planning process helps avoid costly modifications later.
Compliance considerations extend beyond technical implementation to include staff training, documentation requirements, and ongoing monitoring procedures. Organizations benefit from working with local security experts who understand Saudi regulatory landscape and business practices, ensuring alignment with SDAIA’s National Data Management Office requirements.
Training and Change Management
Successful security implementations require thorough user training and change management programs. Employees must understand new security procedures, authentication requirements, and their roles in maintaining organizational security posture.
Training programs should address different user groups, from technical staff who manage security systems to end-users who interact with security controls daily. Regular training updates ensure that staff remain current with evolving security practices and threat landscapes.
Conclusion
Implementing Zero Trust Security solutions represents a strategic investment in organizational resilience and competitive advantage. PIF-backed enterprises that adopt integrated endpoint security strategies position themselves for sustainable growth while protecting valuable assets and stakeholder interests.
The journey toward Zero Trust Security requires careful planning, stakeholder commitment, and ongoing optimization. However, organizations that successfully implement these frameworks gain significant advantages in threat protection, regulatory compliance, and operational efficiency.
Strengthen Your Enterprise Security
Transform your organization’s security posture with enterprise-grade Zero Trust Security solutions tailored for Saudi Arabian enterprises. Contact Alnafitha’s cybersecurity experts to develop a customized security strategy that protects your valuable assets while enabling business growth.