The Kingdom’s ambitious Vision 2030 has fundamentally transformed how Saudi businesses operate, with digital transformation accelerating at an unprecedented pace. Yet beneath this technological renaissance lies a critical challenge that keeps CIOs and IT directors awake at night: implementing effective digital workforce security for an increasingly distributed team structure without compromising productivity or breaking the budget.
The Hidden Cost of Unsecured Endpoints in Saudi Organizations
While most executives focus on the obvious metrics – productivity gains, cost savings, employee satisfaction – they often overlook the exponential risk that comes with each new device connecting to their corporate network. Recent data from Gartner’s cybersecurity research reveals a startling reality: organizations with inadequate endpoint management face an average of 847% higher security incident costs compared to those with robust digital workforce security frameworks.
Consider this: when a marketing manager in Riyadh connects their personal laptop to access client presentations, or when a sales director in Jeddah uses an unmanaged tablet to review contracts during a site visit, each interaction creates potential entry points that traditional perimeter security simply cannot address.
Why Traditional Security Approaches Fail Saudi Arabia’s Digital Workforce
The conventional wisdom of building higher digital walls around corporate data worked perfectly in 2015. Today, it’s not just outdated – it’s counterproductive. Saudi businesses operating across multiple cities and time zones cannot afford security solutions that treat every remote connection as a potential threat requiring manual verification.
The Three Critical Gaps:
Geographic Distribution Complexity: With operations spanning from Riyadh’s financial district to Dammam’s industrial zones, Saudi organizations need endpoint management solutions that work seamlessly across varying network conditions and time zones.
Cultural Integration Requirements: Security protocols that interrupt the natural workflow of Saudi business culture – where relationship-building and collaborative decision-making are paramount – inevitably face resistance and workarounds that create even larger vulnerabilities.
Regulatory Compliance Alignment: The Kingdom’s evolving data protection requirements, particularly around customer financial data and government contracts through SAMA’s cybersecurity framework, demand endpoint solutions that automatically maintain compliance without requiring constant manual oversight.
The Endpoint Management Revolution: Beyond Device Control
Modern digital workforce security isn’t about controlling devices – it’s about intelligently orchestrating the relationship between people, data, and technology. The most successful Saudi organizations are discovering that effective endpoint management creates a competitive advantage rather than merely preventing problems.
Effective Digital Workforce Security Through Smart Device Compliance
Traditional device management approaches Saudi businesses with a binary choice: complete control or complete chaos. Progressive endpoint solutions recognize that different roles require different security postures. The CFO accessing sensitive financial data needs robust encryption and access controls, while the marketing coordinator sharing campaign materials needs flexibility and speed.
The Strategic Approach:
- Risk-Based Authentication: Automatically adjusts security requirements based on data sensitivity and user behavior patterns
- Contextual Access Control: Considers location, time, device health, and network security when granting permissions
- Seamless User Experience: Maintains security without disrupting the natural workflow of Saudi business operations
Data Protection That Scales With Growth
Saudi organizations experiencing rapid growth face a unique challenge: security solutions that work for 50 employees often collapse under the complexity of 500 employees. Effective digital workforce security requires solutions that become more intelligent and efficient as they scale, not more cumbersome.
Key Capabilities for Growing Organizations:
- Automated Compliance Monitoring: Continuously verifies that all endpoints meet organizational security standards without manual intervention
- Intelligent Threat Detection: Uses behavioural analysis to identify potential security incidents before they impact operations
- Centralized Policy Management: Ensures consistent security standards across all locations and departments
Integration Strategy: Making Endpoint Security Work With Existing Infrastructure
The reality facing most Saudi IT departments is stark: they cannot rip out existing systems and start fresh. Effective endpoint management must integrate seamlessly with current directory services, network infrastructure, and business applications while providing immediate security improvements.
Critical Integration Points:
Identity and Access Management Alignment: Modern endpoint solutions must work with existing Microsoft Active Directory, LDAP, or cloud identity providers without requiring users to maintain separate credentials or follow different authentication procedures.
Network Infrastructure Compatibility: Security solutions that require extensive network modifications or create performance bottlenecks will face resistance from both IT teams and end users.
Business Application Integration: Endpoint management must enhance rather than complicate access to critical business applications, whether they’re hosted on-premises, in the cloud, or in hybrid environments.
Cost-Effective Solutions for Saudi Arabia’s Growing Digital Workforce
The misconception that enterprise-grade security requires enterprise-level budgets keeps many Saudi organizations vulnerable. Modern endpoint management solutions offer sophisticated capabilities at price points that make sense for organizations planning sustainable growth.
Financial Strategy Considerations:
Subscription vs. Capital Investment: Cloud-based endpoint management eliminates the need for expensive hardware investments while providing access to continuously updated security capabilities. Leading cloud security platforms offer enterprise-grade protection with flexible pricing models.
Scalability Economics: Solutions that offer per-user pricing models align costs with growth, making it easier to budget for expansion while maintaining consistent security standards. Alnafitha’s endpoint management solutions provide this exact flexibility for growing Saudi businesses.
Total Cost of Ownership: Automated management capabilities reduce the ongoing IT support requirements, often providing cost savings that offset the solution investment within the first year.
The Competitive Advantage of Proactive Digital Workforce Security
Saudi organizations that implement comprehensive endpoint management don’t just reduce security risks – they create operational advantages that directly impact their competitive position. When employees can securely access corporate resources from any device, anywhere, at any time, the entire organization becomes more agile and responsive.
Business Impact Areas:
Client Service Enhancement: Field sales teams and client service representatives can access real-time data and applications, improving response times and service quality.
Operational Efficiency: Reduced IT support requests and automated compliance management free technical resources to focus on strategic initiatives rather than maintenance tasks.
Talent Attraction and Retention: Flexible, secure remote work capabilities help attract top talent and reduce employee turnover in Saudi Arabia’s competitive job market.
Implementation Roadmap: From Assessment to Optimization
Successful digital workforce security implementation follows a structured approach that minimizes disruption while maximizing security improvements. Organizations that attempt to implement comprehensive endpoint management overnight often create more problems than they solve.
Implementation Roadmap
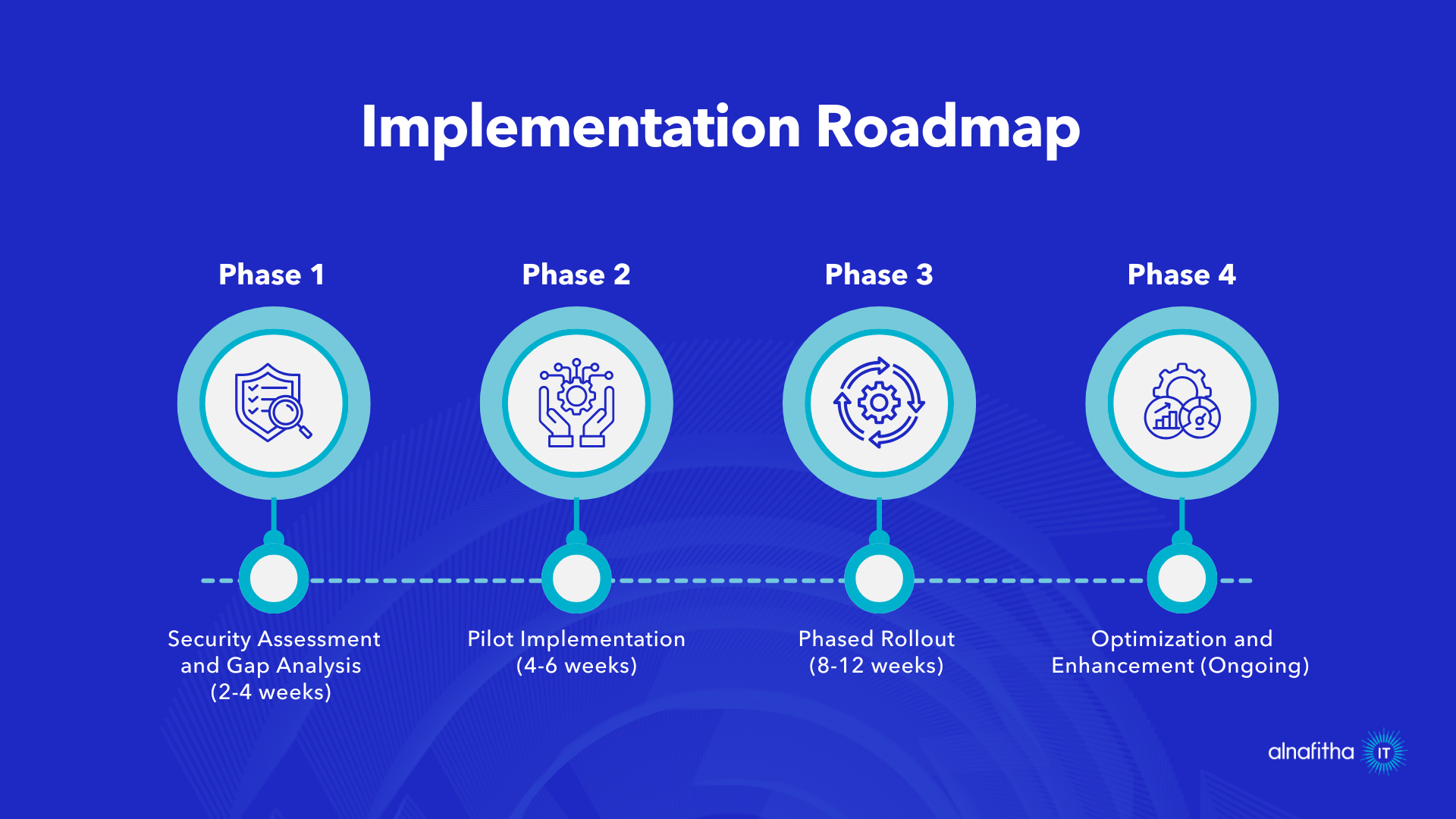
Phase 1: Security Assessment and Gap Analysis (2-4 weeks)
- Document current endpoint inventory and security postures
- Identify critical data flows and access requirements
- Assess integration requirements with existing infrastructure
Phase 2: Pilot Implementation (4-6 weeks)
- Deploy endpoint management for a select group of users
- Test integration with critical business applications
- Refine policies and procedures based on real-world usage
Phase 3: Phased Rollout (8-12 weeks)
- Gradually expand coverage across departments and locations
- Monitor performance and user satisfaction metrics
- Adjust configurations based on operational feedback
Phase 4: Optimization and Enhancement (Ongoing)
- Analyze security and performance data to identify improvement opportunities
- Expand capabilities as organizational needs evolve
- Maintain compliance with changing regulatory requirements
The Future of Digital Workforce Security in Saudi Arabia
As the Kingdom continues its digital transformation journey, the organizations that thrive will be those that view endpoint management not as a necessary expense, but as a strategic enabler of business growth. The question isn’t whether Saudi businesses need modern digital workforce security – it’s whether they can afford to delay implementation while their competitors gain operational advantages.
The most successful endpoint management initiatives share a common characteristic: they make security invisible to end users while providing comprehensive protection for organizational assets. When employees can focus on serving clients and driving growth rather than navigating security procedures, the entire organization benefits.
Strategic Digital Workforce Security Planning for Saudi Business Leaders:
The digital workforce security solutions implemented today will determine which organizations can effectively compete in tomorrow’s increasingly connected business environment. Those that choose proactive, intelligent endpoint management will find themselves better positioned to capitalize on emerging opportunities while maintaining the trust and confidence of their clients and partners.
Smart endpoint management isn’t about implementing the latest technology – it’s about creating a secure foundation that enables Saudi organizations to pursue their growth ambitions with confidence, knowing that their digital workforce can operate effectively regardless of location, device, or network conditions.
In an era where business agility determines market success, comprehensive digital workforce security has evolved from a compliance requirement to a competitive necessity. The organizations that recognize this shift earliest will be the ones that define the future of business operations in the Kingdom.
Implement Digital Workforce Security for Your Growing Business Now
Don’t let endpoint security challenges slow down your growth. Every day without proper digital workforce protection puts your business at risk and limits your competitive potential.
Take Action Today:
Saudi businesses across industries – from manufacturing in Jubail to technology startups in NEOM – trust expert guidance to navigate their digital security transformation. Whether you’re managing 50 employees or 500, the right endpoint management strategy can transform security from a business constraint into a competitive advantage.
Your next strategic move starts with understanding exactly what your organization needs. Get a personalized assessment of your current digital workforce security posture and discover the specific solutions that will drive your business forward.
Schedule Your Free Security Assessment Today →
Ready to join Saudi Arabia’s most secure and agile organizations? Our cybersecurity experts are standing by to show you exactly how endpoint management can accelerate your business growth while keeping your data completely protected.
