In today’s rapidly evolving energy landscape, smart grid security has become a paramount concern for energy organizations across Saudi Arabia. The Saudi Arabia Smart Grid Network Market was valued at USD 765.59 Million in 2023, and is expected to reach USD 1.77 billion by 2029, rising at a CAGR of 14.92%. As the Kingdom advances toward its Vision 2030 goals, this massive investment underscores the critical importance of implementing robust identity management systems to protect these valuable digital assets.
Bottom Line Up Front: With Saudi Arabia investing $1.77 billion in smart grid infrastructure by 2029, implementing comprehensive identity management systems isn’t just a security necessity—it’s essential for protecting the Kingdom’s energy transformation and economic diversification under Vision 2030.
Understanding the Smart Grid Security Landscape in Saudi Arabia
The modern smart grid represents a complex ecosystem of interconnected devices, sensors, and control systems that enable efficient energy distribution and management. However, this digital transformation also introduces new vulnerabilities that require sophisticated energy infrastructure protection strategies aligned with international best practices such as the NIST Cybersecurity Framework and IEC 62443 industrial cybersecurity standards.
Saudi Arabia faces unique cybersecurity challenges as it modernizes its grid infrastructure. In the year 2023 alone, there was an increase by thirty percent (30%) in cyber-attacks within Saudi Arabia where the majority were targeted at finance and health sectors. The increasing number of connected devices, from smart meters to automated substations, creates multiple entry points for potential cyber threats. More than 110 million cyberattacks have been witnessed in the last few years in Saudi Arabian industries like; healthcare, finance, and oil, highlighting the urgent need for comprehensive critical infrastructure cybersecurity measures.
The smart grid network, with its extensive data collection and communication capabilities, is vulnerable to various cyber risks, including data breaches, hacking, and system manipulations. Without proper security frameworks that comply with ISO 27001 information security standards, these vulnerabilities can compromise entire energy networks, affecting both operational efficiency and national security.
The Economic Impact: Saudi Arabia’s Cybersecurity Investment
The Kingdom’s commitment to smart grid security reflects significant economic considerations. The Saudi Arabian cybersecurity market is valued at 13.3 billion Saudi Riyals, with government entities contributing 31% (4.1 billion Saudi Riyals) and the private sector contributing 69% (9.2 billion Saudi Riyals). The cybersecurity sector contributes 0.39% to the Kingdom’s overall GDP and 0.81% to the non-oil GDP, with a total economic impact of 15.6 billion Saudi Riyals.
Furthermore, Saudi Arabia is on the precipice of becoming a regional powerhouse in cybersecurity as the market is expected to surge from USD 4.63 billion in 2024 to USD 6.65 billion by 2029, reflecting a strong compound annual growth rate (CAGR) of 7.52% over the next five years. This growth is propelled by an increasing dependency on digital technologies and heightened network security threats, particularly as the energy sector embraces smart grid technologies.
The Foundation of Smart Grid Security: Identity Management
Identity management systems serve as the cornerstone of comprehensive smart grid security. These systems ensure that only authorized personnel and devices can access critical energy infrastructure components. Understanding what identity and access management entails, its components, capabilities, and benefits is fundamental for energy organizations. In the context of Saudi Arabia’s energy sector, implementing robust identity and access management solutions becomes even more crucial due to the scale and importance of the Kingdom’s energy operations.
Saudi Arabia ranks first globally in cybersecurity for 2025, with the UN’s International Telecommunication Union also naming Saudi Arabia a Tier 1 “role-modeling” nation in its Global Cybersecurity Index 2024. This achievement underscores the importance of maintaining advanced identity management systems that meet international standards while supporting the Kingdom’s continued leadership in cybersecurity excellence.
Key Components of Energy Infrastructure Identity Management
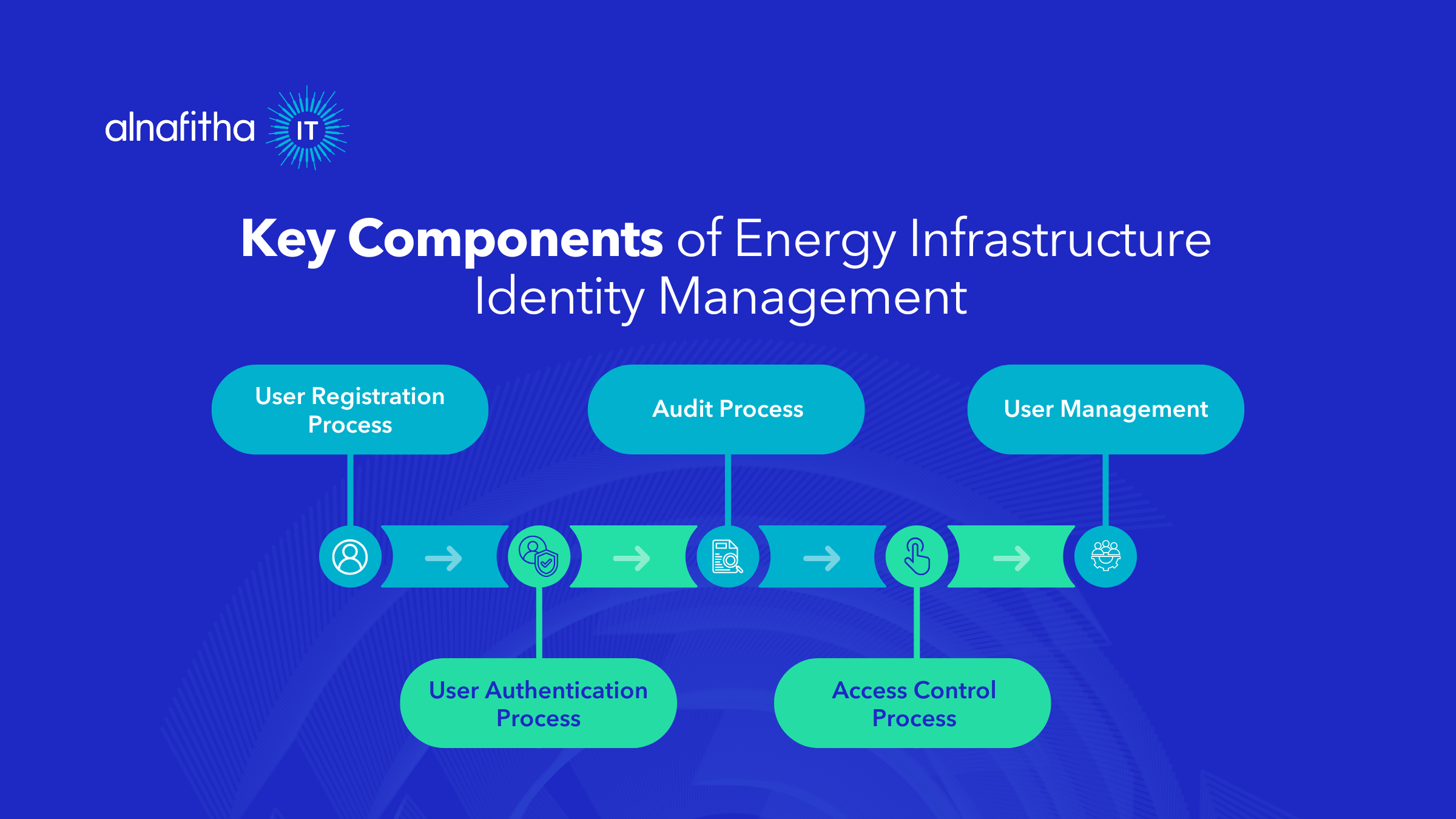
Authentication and Authorization Controls Modern identity management systems must provide multi-layered authentication mechanisms that verify both human users and connected devices. This includes implementing strong password policies, multi-factor authentication, and device certificates that align with Saudi Arabia’s regulatory requirements and industry best practices established by the National Cybersecurity Authority (NCA). These controls must follow international frameworks like the NIST Guidelines for Smart Grid Cybersecurity to ensure comprehensive protection.
Access Control and Privilege Management Effective energy infrastructure protection requires granular control over who can access what systems and when. Role-based access control (RBAC) ensures that grid operations teams, maintenance personnel, and administrative staff have appropriate permissions based on their responsibilities and operational needs. Implementing comprehensive network security solutions helps organizations maintain these critical access controls while ensuring operational efficiency and compliance with international standards.
Continuous Monitoring and Threat Detection Advanced critical infrastructure cybersecurity solutions must include real-time monitoring capabilities that can detect unusual access patterns, unauthorized login attempts, and potential security breaches before they escalate into major incidents. Organizations should implement comprehensive endpoint and application security measures to protect against evolving threats targeting smart grid infrastructure, following guidelines from established frameworks.
Implementing Smart Grid Security Best Practices
Establishing a Comprehensive Security Framework
Organizations in Saudi Arabia’s energy sector should develop a holistic approach to smart grid security that encompasses both technical and operational elements. This framework should align with international standards while considering local regulatory requirements established by the Ministry of Energy and cultural factors specific to the Kingdom’s business environment.
Risk Assessment and Vulnerability Management Regular security assessments help identify potential weaknesses in identity management systems and overall energy infrastructure protection strategies. These assessments should evaluate both technical vulnerabilities and human factors that could compromise security. Implementing robust risk and compliance frameworks ensures organizations maintain comprehensive oversight of their security posture while meeting regulatory requirements and international best practices.
Incident Response and Recovery Planning Robust critical infrastructure cybersecurity requires preparation for potential security incidents. Organizations must develop comprehensive incident response plans that include clear communication protocols, recovery procedures, and lessons learned documentation that align with both local NCA requirements and international standards.
Integration with Existing Energy Systems
Successful implementation of identity management systems requires careful integration with existing energy infrastructure. This process should minimize disruption to daily operations while ensuring comprehensive security coverage across all critical systems, following established protocols from international cybersecurity frameworks.
Legacy System Considerations Many energy organizations in Saudi Arabia operate a mix of modern and legacy systems. Effective smart grid security strategies must address the unique challenges of protecting older infrastructure while enabling digital transformation initiatives that support Vision 2030 objectives.
Scalability and Futureproofing as Saudi Arabia’s energy infrastructure continues to evolve, identity management systems must be designed to scale with growing demands and adapt to emerging technologies and threats identified in international security guidelines and best practices.
Regulatory Compliance and Standards
Saudi Arabian Regulatory Environment
Energy organizations must ensure their identity management systems comply with relevant Saudi Arabian regulations and standards. This includes understanding requirements from the Saudi Arabian Monetary Authority (SAMA), the National Cybersecurity Authority (NCA), and other relevant regulatory bodies. The NCA’s Essential Cybersecurity Controls (ECC-2) provide comprehensive guidelines for protecting critical infrastructure, including specific requirements for identity and access management in energy sector organizations.
International Standards Alignment Implementing energy infrastructure protection measures that align with international standards such as ISO 27001, NIST Cybersecurity Framework, and IEC 62443 helps ensure comprehensive security coverage and facilitates international partnerships while meeting the Kingdom’s high cybersecurity standards.
Continuous Improvement and Adaptation
The cybersecurity landscape evolves rapidly, requiring organizations to continuously update their smart grid security strategies. Regular reviews of identity management systems and critical infrastructure cybersecurity measures ensure ongoing effectiveness against emerging threats while maintaining compliance with both local and international security standards.
Real-World Success: Saudi Arabia’s Smart Grid Transformation
Saudi Arabia’s commitment to smart grid security is already showing tangible results. The Saudi Electric Company has successfully deployed approximately 11 million smart meters by 2022, with plans to install 12 million smart meters by 2025. This massive infrastructure deployment requires sophisticated identity management systems to ensure secure device authentication and data protection across the entire network.
The Kingdom’s smart grid automation has reached 32% of the electricity distribution network, demonstrating the practical implementation of advanced critical infrastructure cybersecurity measures. This progress supports Saudi Arabia’s Vision 2030 goal of generating 50% of electricity from renewable sources, requiring robust security frameworks to manage the complexity of distributed energy resources while maintaining the highest international security standards.
Technology Solutions and Implementation
Selecting the Right Identity Management Platform
Choosing appropriate identity management systems requires careful evaluation of technical capabilities, scalability, and integration requirements. Organizations should consider solutions that offer comprehensive authentication and authorization capabilities, integration with existing energy management systems, scalability to support growing infrastructure needs, and compliance with relevant security standards and regulations including international frameworks.
Deployment Strategies
Successful implementation of energy infrastructure protection measures requires phased deployment strategies that minimize operational disruption while ensuring comprehensive security coverage that meets both local and international cybersecurity standards.
Pilot Programs and Gradual Rollout Starting with pilot programs allows organizations to test and refine their smart grid security approaches before full-scale implementation across critical infrastructure, ensuring alignment with established best practices and regulatory requirements.
Measuring Success and ROI
Key Performance Indicators
Organizations should establish clear metrics to evaluate the effectiveness of their identity management systems and overall critical infrastructure cybersecurity investments. These metrics should include security incident reduction rates, access control compliance levels, system availability and performance metrics, and user satisfaction and operational efficiency indicators that demonstrate adherence to international security standards.
Long-term Value Creation
Effective energy infrastructure protection strategies create long-term value through reduced security risks, improved operational efficiency, and enhanced regulatory compliance. Organizations should track these benefits to demonstrate the return on investment in smart grid security initiatives while maintaining alignment with Vision 2030 objectives.
Future Considerations and Emerging Trends
Artificial Intelligence and Machine Learning
Advanced identity management systems are increasingly incorporating AI and ML capabilities to enhance threat detection and response capabilities. These technologies can help identify unusual access patterns and potential security threats before they impact critical energy infrastructure, following guidance from international cybersecurity frameworks.
Cloud Integration and Hybrid Architectures
As Saudi Arabia’s energy sector embraces cloud technologies, critical infrastructure cybersecurity strategies must evolve to address hybrid cloud environments while maintaining strong security controls that comply with both local regulations and international standards.
Partnering for Success: Expert Implementation Support
Implementing comprehensive smart grid security solutions requires specialized expertise and deep understanding of both international best practices and local regulatory requirements. Organizations seeking to enhance their identity management systems and energy infrastructure protection capabilities can benefit from partnering with experienced cybersecurity professionals who understand the unique challenges of the Saudi energy sector.
From initial risk assessments and compliance audits to full-scale implementation of advanced security frameworks, expert guidance ensures that critical infrastructure cybersecurity initiatives align with both operational needs and regulatory expectations. This includes developing customized identity and access management solutions, implementing robust network security measures, establishing comprehensive endpoint and application security, and creating effective risk and compliance programs that support long-term business objectives while maintaining alignment with international cybersecurity standards.
Conclusion
Securing Saudi Arabia’s smart grid infrastructure requires a comprehensive approach that places identity management systems at the center of energy infrastructure protection strategies. By implementing robust authentication, authorization, and monitoring capabilities that align with international standards and local regulatory requirements, energy organizations can protect their critical assets while enabling operational excellence and supporting the Kingdom’s Vision 2030 objectives.
The journey toward comprehensive smart grid security requires commitment, investment, and ongoing attention to emerging threats and technologies. However, organizations that prioritize critical infrastructure cybersecurity today will be better positioned to thrive in tomorrow’s digital energy landscape while maintaining Saudi Arabia’s leadership position in global cybersecurity excellence.
Success in this endeavor depends on selecting the right technologies, implementing appropriate policies and procedures, and fostering a culture of security awareness throughout the organization. With proper planning and execution, identity management systems can serve as the foundation for a secure, efficient, and resilient smart grid infrastructure that supports Saudi Arabia’s energy future while meeting the highest international security standards.
Secure Your Energy Infrastructure
Don’t let cybersecurity vulnerabilities compromise your critical energy operations. As Saudi Arabia continues its digital transformation under Vision 2030, ensuring robust smart grid security isn’t just an option—it’s essential for operational continuity and national security.
Take Action Today:
- Assess your current identity management capabilities
- Identify gaps in your cybersecurity framework
- Implement comprehensive protection strategies
- Ensure compliance with NCA requirements and international standards
Contact our cybersecurity experts to schedule a comprehensive risk assessment and discover how advanced identity management solutions can protect your critical energy infrastructure while supporting your Vision 2030 objectives.
