As Saudi Arabia accelerates digital transformation under Vision 2030, cybersecurity has become a strategic imperative. Traditional security models based on network perimeter assumptions are proving inadequate. To reduce the risk of breaches and insider threats, Saudi organizations are adopting a modern security strategy: Zero Trust architecture.
This guide offers a practical breakdown of how implementing Zero Trust helps improve your security posture, comply with Saudi data privacy regulations, and build robust protection across cloud environments, remote teams, and IoT devices.
What is Zero Trust Architecture?
The Zero Trust model operates on a simple yet powerful principle: “Never trust, always verify.” No user or device is trusted automatically—regardless of location. Instead, every access request is verified in real time, based on identity, device health, and context.
This shift from implicit trust to a trust approach that continuously validates identity ensures organizations can securely support remote working, cloud adoption, and mobility.
Additionally, for a general overview, refer to this Wikipedia article on Zero Trust architecture to understand its core principles and evolution.
Why Saudi Organizations Need a Zero Trust Framework
The cybersecurity threat landscape in Saudi Arabia is rapidly evolving. Factors like BYOD, increased network traffic from cloud apps, and the rise of IoT devices mean traditional firewalls alone can’t protect sensitive data.
Moreover, events like Ramadan often bring spikes in phishing and ransomware attacks targeting critical sectors including healthcare, finance, and logistics. That’s why the Saudi National Cybersecurity Authority (NCA) advocates adopting a Zero Trust framework as a national best practice.
Key benefits include:
- Minimizing breach risks through access control and continuous monitoring.
- Supporting Saudi data privacy compliance.
- Enhancing granting access protocols for employees and third parties.
- Establishing visibility across all users and devices.
To complement this approach, explore our Top 10 Information Security Practices for Saudi Businesses
Step-by-Step Guide to Implementing Zero Trust
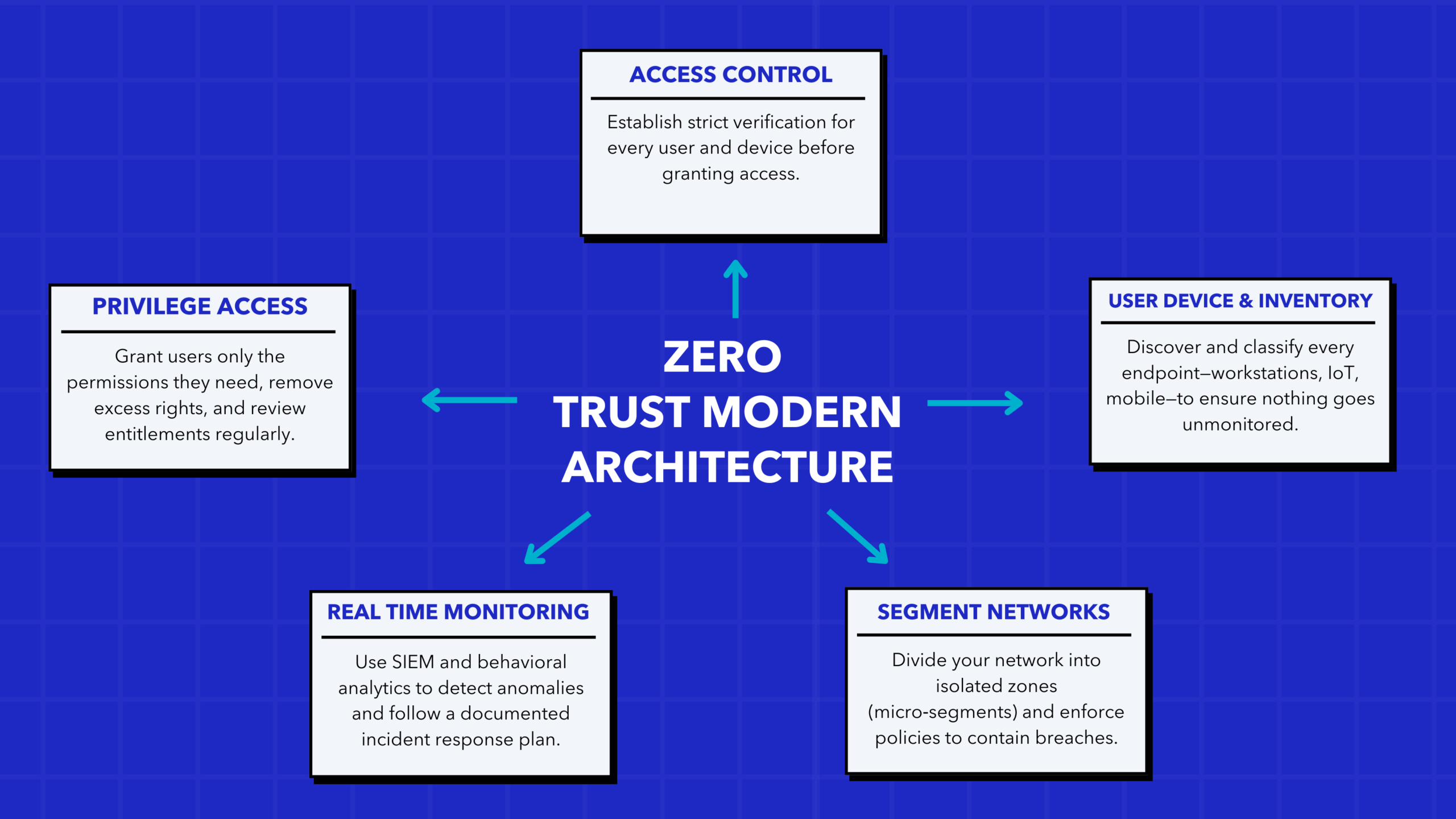
1. Identity and Access Management
Begin by establishing robust identity and access management protocols to verify every user or device attempting to access your systems.
Key Actions:
- Implement Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring multiple forms of verification.
- Utilize Identity Platforms: Solutions like Microsoft Entra ID (formerly Azure AD) can streamline identity management.
- Define Role-Based Access Controls (RBAC): Ensure users have access only to the resources necessary for their roles.
Learn more about our identity access management solutions.
2. Inventory All Users and Devices
You must know every user or device connected to your network before applying any controls.
Key Actions:
- Deploy endpoint management tools to detect IoT devices and unmanaged assets.
- Next, classify data based on sensitivity and compliance needs.
- Additionally, pinpoint systems that process regulated data under Saudi data privacy compliance.
Explore how enterprise risk management can help identify and address infrastructure compliance gaps.
3. Network Segmentation
Limit potential intruder movement within your network through effective network segmentation.
Key Actions:
- Implement Micro-Segmentation: Divide the network into isolated segments to contain potential breaches.
- Furthermore, establish Clear Access Policies: Define and enforce rules governing network traffic between segments.
- Finally, utilize Advanced Firewalls: Deploy firewalls to monitor and control traffic flow between segments.
Learn more about what network segmentation is and why it matters for Zero Trust security.
4. Enforce Least Privilege Access
Only allow user access necessary to perform tasks—no more, no less.
Key Actions:
- Eliminate excessive admin privileges.
- Use Just-in-Time (JIT) access controls for sensitive environments.
- Perform periodic entitlement reviews.
For guidance on policy enforcement and role-based security, Get expert help with access control
5. Continuous Monitoring and Real-Time Response
Implement systems to monitor activities and respond to threats in real time.
Key Actions:
- Deploy Security Information and Event Management (SIEM) Systems: Aggregate and analyse security data to detect anomalies.
- Utilize Behavioural Analytics: Identify unusual patterns indicative of potential threats.
- Establish Incident Response Protocols: Develop and regularly update procedures for responding to security incidents.
Learn how to boost threat detection with SIEM to enhance your real-time monitoring capabilities.
Common Zero Trust Implementation Pitfalls
Avoid these missteps:
- Treating Zero Trust as a one-time software purchase.
- Another mistake is Over-engineering access control systems to the point of user friction.
- Many organizations also fail to secure executive buy-in.
- Lastly, neglecting user training on new security measures can undermine implementation efforts
Strategic Security Implementation: The Business Value of Zero Trust
Zero Trust architecture offers more than protection—it consequently enables business growth in a secure, scalable way. As a result, It helps Saudi organizations navigate the challenges of cloud services, mobility, and regulatory compliance without compromising user experience.
Therefore, by adopting a Zero Trust framework, sectors such as government, energy, and healthcare can:
- Strengthen their security posture.
- Moreover, simplify cloud environments and modernization efforts.
- As a result, build digital trust with citizens, clients, and stakeholders.
Conclusion
As Saudi Arabia continues its ambitious journey toward digital transformation under Vision 2030, implementing Zero Trust architecture represents a critical evolution in cybersecurity strategy. The traditional security perimeter has dissolved, and organizations must adapt to protect their digital assets in this new landscape.
By embracing the “never trust, always verify” principle, Saudi organizations can significantly reduce their vulnerability to both external threats and insider risks. This approach not only strengthens security but also enables the agility and innovation necessary for digital transformation.
Zero Trust is not merely a technology solution but a comprehensive security framework that requires ongoing commitment, continuous assessment, and cultural adaptation. While the implementation journey may present challenges, the benefits—enhanced security posture, improved compliance with Saudi data privacy regulations, and greater operational resilience—far outweigh the investment.
As cyber threats continue to evolve in sophistication and scale, Zero Trust architecture provides Saudi organizations with a robust foundation to protect their most valuable assets while enabling secure digital innovation across all sectors of the economy.
Get Started with a Trusted Security Strategy
At Alnafitha IT, we help organizations strengthen their cybersecurity posture through strategic consulting and enterprise-grade security solutions. Our experts work with you to assess your current infrastructure, align with Saudi cybersecurity standards, and implement best practices—including principles of the Zero Trust model—to secure your environment from the inside out.