As Saudi Arabia accelerates its digital transformation under Vision 2030, businesses across the Kingdom face increasingly sophisticated cyber threats. Network segmentation has emerged as a critical security strategy for protecting sensitive data, ensuring compliance, and maintaining operational resilience. This comprehensive guide explores how Saudi organizations can implement effective network segmentation strategies to safeguard their critical infrastructure.
What is Network Segmentation and Why Does It Matter?
Network segmentation is the practice of dividing a computer network into smaller, isolated segments or subnetworks, each functioning as its own secure zone. Think of it as creating separate rooms in a building with controlled access points, rather than having one massive open space where everyone can access everything.
For Saudi businesses, especially those in critical sectors like energy, healthcare, finance, and government services, network segmentation provides essential protection against cyber attacks, ransomware, and data breaches. When properly implemented, network segmentation ensures that even if attackers breach one segment, they cannot freely move laterally across your entire network.
The Business Case for Network Segmentation in Saudi Arabia
Enhanced Security Posture
Network segmentation dramatically reduces your attack surface. According to Cisco’s security research, organizations with proper network segmentation can contain breaches 80% faster than those without it. For Saudi enterprises handling sensitive customer data or operating critical infrastructure, this containment capability is invaluable.
Regulatory Compliance
The Saudi National Cybersecurity Authority (NCA) has established stringent Essential Cybersecurity Controls (ECC) that many organizations must follow. Network segmentation is fundamental to meeting these compliance requirements, particularly for organizations handling personal data under the Personal Data Protection Law (PDPL).
Alnafitha’s cybersecurity solutions help Saudi businesses implement network segmentation strategies aligned with NCA requirements, ensuring both security and compliance.
Improved Network Performance
Beyond security, network segmentation optimizes network performance by reducing congestion. When you implement network segmentation, you limit broadcast traffic to specific segments, improving overall network efficiency—crucial for Saudi businesses managing high-volume transactions or real-time operations.
Types of Network Segmentation for Saudi Businesses
Physical Network Segmentation
Physical network segmentation involves using separate physical hardware—switches, routers, and cables—to create distinct network segments. While this approach offers the strongest security, it’s also the most expensive and least flexible.
For Saudi enterprises with dedicated data centers, physical network segmentation may be appropriate for isolating the most sensitive systems, such as financial transaction processors or patient health records.
Virtual Network Segmentation (VLAN)
Virtual Local Area Networks (VLANs) provide network segmentation through software configuration rather than physical separation. VLAN network segmentation is cost-effective and flexible, making it ideal for growing Saudi businesses.
With VLAN network segmentation, you can:
- Separate departments (finance, HR, operations)
- Isolate guest networks from corporate resources
- Segment IoT devices from critical business systems
- Create dedicated segments for compliance requirements
Micro-Segmentation
Micro-segmentation represents the most granular approach to network segmentation, creating security zones down to the individual workload level. This advanced network segmentation strategy is particularly valuable for Saudi organizations embracing cloud technologies and zero-trust security models.
Alnafitha’s network solutions can help implement micro-segmentation strategies tailored to your specific business requirements.
Key Benefits of Network Segmentation for Saudi Organizations
Damage Containment and Access Control
The primary benefit of network segmentation is containment. When ransomware or malware infiltrates your network, network segmentation prevents it from spreading throughout your entire infrastructure. This is especially critical for Saudi critical infrastructure providers where a widespread breach could have catastrophic consequences.
Network segmentation also enables precise access control. You can ensure that employees only access the network segments necessary for their roles, implementing the principle of least privilege—a core tenet of modern cybersecurity recommended by NIST.
Enhanced Monitoring and Threat Detection
Network segmentation simplifies security monitoring. Instead of trying to monitor all traffic across a flat network, security teams can focus on traffic patterns between segments. Unusual cross-segment traffic often indicates a security incident, enabling faster threat detection.
For Saudi businesses, this improved visibility is essential for meeting NCA’s continuous monitoring requirements and responding quickly to emerging threats.
Reduced Compliance Scope
Network segmentation can significantly reduce the scope and cost of compliance audits. For example, if your organization processes credit card payments, network segmentation allows you to isolate the cardholder data environment (CDE), limiting PCI DSS compliance requirements to just that segment rather than your entire network.
Similarly, Saudi healthcare providers can use network segmentation to separate systems containing patient health information, simplifying HIPAA or local privacy compliance efforts.
Network Segmentation Best Practices for Saudi Businesses
Conduct a full-scale Network Assessment
Before implementing network segmentation, thoroughly map your existing network infrastructure. Identify:
- Critical assets and sensitive data locations
- Current traffic patterns and data flows
- Existing security controls and gaps
- Compliance requirements and obligations
Alnafitha’s professional services offer full network assessments to help Saudi businesses understand their current security posture and plan effective network segmentation strategies.
Define Clear Segmentation Policies
Effective network segmentation requires clear policies defining:
- What resources belong in each segment
- Who can access each segment
- What communication is permitted between segments
- How exceptions are handled and documented
Your network segmentation policies should align with your organization’s risk tolerance, operational requirements, and compliance obligations.
Implement Zero Trust Principles
Modern network segmentation strategies embrace zero trust principles—never trust, always verify. Rather than assuming everything inside your network perimeter is safe, zero trust network segmentation requires authentication and authorization for every access request, regardless of location.
For Saudi organizations, zero trust network segmentation is particularly valuable as workforces become more distributed and cloud adoption increases.
Use Firewalls and Access Control Lists (ACLs)
Deploy next-generation firewalls at segment boundaries to control and monitor traffic. Network segmentation effectiveness depends on properly configured ACLs that specify exactly what traffic is permitted between segments.
According to Palo Alto Networks, organizations should regularly review and update these rules to prevent policy drift and maintain effective network segmentation.
Monitor and Test Regularly
Network segmentation isn’t a one-time project—it requires ongoing monitoring and testing. Regularly:
- Review segment access logs for anomalies
- Test segmentation controls to verify effectiveness
- Update policies as business needs evolve
- Conduct penetration testing across segment boundaries
Network Segmentation for Specific Saudi Industry Sectors
Energy and Utilities
Saudi Arabia’s energy sector faces unique cybersecurity challenges. Network segmentation for oil, gas, and utilities companies should separate:
- Operational Technology (OT) from Information Technology (IT) networks
- SCADA systems from corporate networks
- Remote field operations from central management
- Safety-critical systems from general business systems
Proper network segmentation in this sector can prevent cyber attacks from disrupting critical energy infrastructure that the Kingdom and global markets depend upon.
Financial Services
Saudi banks and financial institutions handle enormous volumes of sensitive financial data. Network segmentation strategies for this sector should include:
- Separation of customer-facing applications from backend systems
- Isolation of payment processing environments
- Segmentation of ATM and point-of-sale networks
- Dedicated segments for mobile banking infrastructure
Network segmentation helps Saudi financial institutions meet both NCA requirements and international standards like PCI DSS and ISO 27001.
Healthcare Providers
As Saudi Arabia expands its healthcare capabilities, protecting patient data becomes increasingly critical. Healthcare network segmentation should isolate:
- Electronic health record systems
- Medical IoT devices and equipment
- Pharmaceutical inventory systems
- Administrative and billing systems
Government and Public Sector
Saudi government entities manage highly sensitive citizen data and critical services. Network segmentation for public sector organizations should create distinct zones for:
- Classified information systems
- Citizen-facing service portals
- Inter-agency communication networks
- Administrative functions
Robust network segmentation helps government agencies meet NCA’s elevated security requirements while maintaining service accessibility.
Common Network Segmentation Challenges and Solutions
Complexity Management
Network segmentation can become complex, especially in large organizations. The solution is to:
- Start with the most critical assets
- Document everything thoroughly
- Use network visualization tools
- Implement gradually rather than all at once
Legacy System Integration
Many Saudi businesses operate legacy systems that weren’t designed with network segmentation in mind. Address this by:
- Creating dedicated legacy segments with strict controls
- Planning phased modernization
- Using security gateways to bridge old and new systems
- Prioritizing the isolation of the most vulnerable legacy systems
Performance Concerns
Some organizations worry that network segmentation will impact performance. However, proper implementation actually improves performance by:
- Reducing broadcast traffic
- Optimizing traffic routing
- Preventing network congestion
- Enabling better bandwidth allocation
Cost Considerations
While network segmentation requires investment, the cost of NOT implementing it—potential breaches, downtime, regulatory fines—far exceeds implementation costs. Additionally, VLAN-based network segmentation provides strong security at reasonable cost for most Saudi businesses.
Network Segmentation and Zero Trust Architectures
Network segmentation forms the foundation of zero trust security architectures. As Saudi organizations adopt cloud services and support remote work, combining network segmentation with zero trust principles creates defense in depth:
- Network segmentation divides your infrastructure into security zones
- Zero trust ensures every access request is authenticated and authorized
- Micro-segmentation extends security to individual workloads
- Continuous monitoring detects anomalous behavior across segments
This layered approach aligns with CISA’s zero trust maturity model and provides comprehensive protection for Saudi critical infrastructure.
Implementing Network Segmentation: A Roadmap for Saudi Businesses
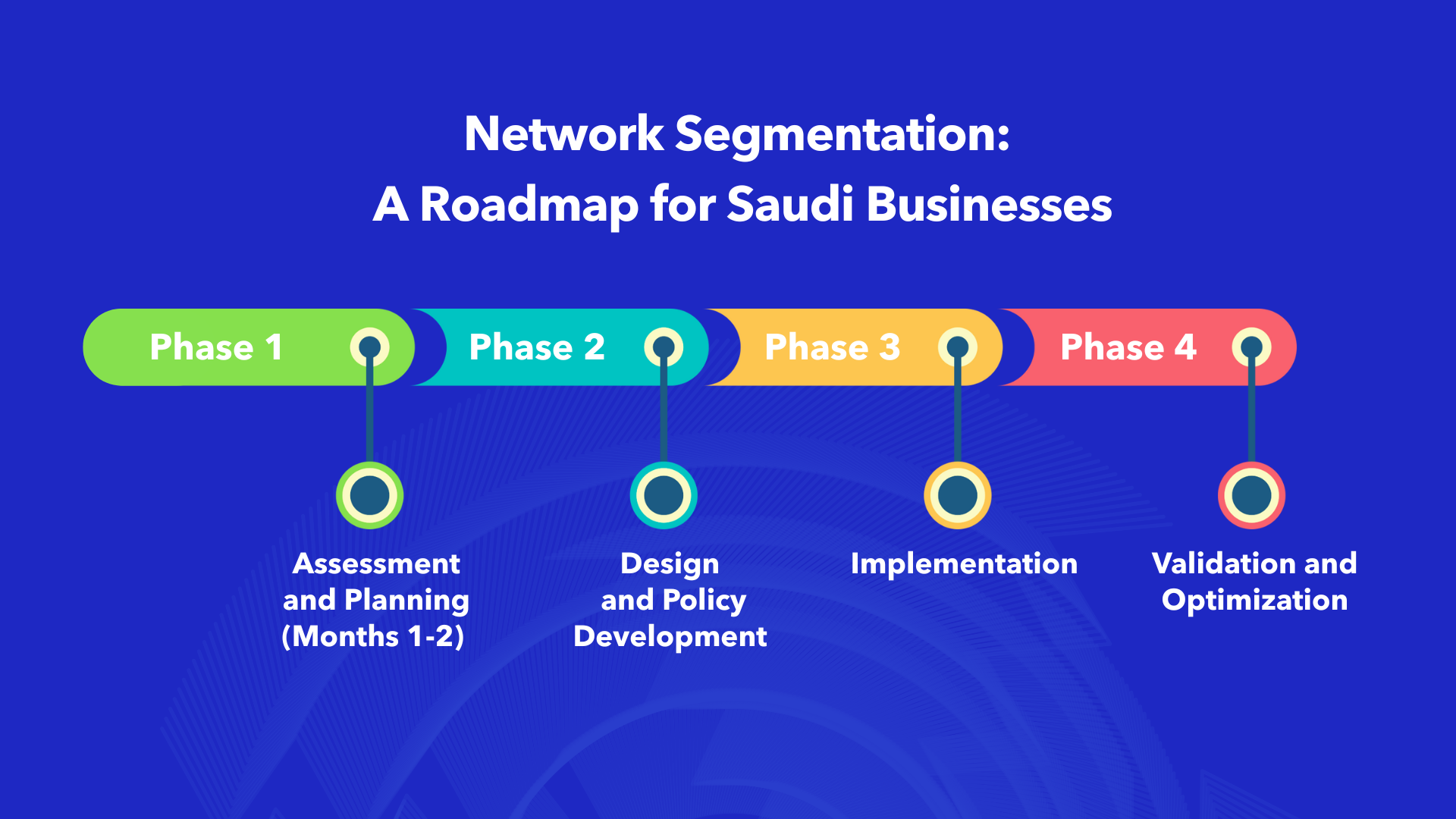
Phase 1: Assessment and Planning (Months 1-2)
- Conduct comprehensive network discovery
- Identify critical assets and sensitive data
- Map current traffic flows and dependencies
- Define network segmentation objectives and success criteria
- Develop detailed network segmentation architecture
Phase 2: Design and Policy Development
- Design segment structure and boundaries
- Create access control policies for each segment
- Define inter-segment communication rules
- Plan firewall and security control placement
- Document network segmentation standards and procedures
Phase 3: Implementation
- Begin with the most critical segments
- Deploy VLANs, firewalls, and access controls
- Implement monitoring and logging systems
- Test network segmentation effectiveness
- Train IT staff on new network segmentation architecture
Phase 4: Validation and Optimization
- Conduct penetration testing across segment boundaries
- Review and refine access policies
- Optimize performance and security configurations
- Expand network segmentation to additional systems
- Establish ongoing monitoring and maintenance procedures
Alnafitha’s expert team can guide Saudi businesses through each phase of network segmentation implementation, ensuring your investment delivers maximum security value.
The Future of Network Segmentation in Saudi Arabia
As Saudi Arabia continues its digital transformation journey, network segmentation will evolve alongside emerging technologies:
Software-Defined Networking (SDN)
SDN enables dynamic network segmentation that automatically adjusts to changing business needs and threat landscapes. Saudi enterprises adopting SDN can implement more flexible, responsive network segmentation strategies.
AI-Powered Segmentation
Artificial intelligence and machine learning will enhance network segmentation by:
- Automatically classifying assets and assigning appropriate segments
- Detecting anomalous cross-segment traffic patterns
- Recommending policy adjustments based on usage patterns
- Predicting potential security risks before they materialize
Cloud-Native Segmentation
As Saudi businesses embrace public cloud, hybrid cloud, and multi-cloud strategies, network segmentation must extend seamlessly across on-premises and cloud environments. Cloud-native network segmentation tools will become essential for maintaining consistent security policies everywhere.
Conclusion: Network Segmentation as a Business Imperative
For Saudi businesses, network segmentation is no longer optional—it’s a fundamental requirement for protecting critical assets, ensuring regulatory compliance, and maintaining customer trust. Whether you operate in energy, finance, healthcare, government, or any other sector, effective network segmentation provides the foundation for a robust cybersecurity posture.
The good news is that network segmentation doesn’t require a complete infrastructure overhaul. By starting with your most critical assets and implementing network segmentation incrementally, you can significantly improve security while managing costs and minimizing disruption.
As cyber threats continue to evolve and Saudi Arabia’s regulatory environment becomes more stringent, organizations that invest in proper network segmentation today will be better positioned for secure growth tomorrow.
Ready to implement network segmentation for your Saudi business?
Contact Alnafitha today to discuss how our cybersecurity experts can design and deploy a network segmentation strategy for your organization’s unique requirements, ensuring your critical infrastructure remains secure in an increasingly connected world.
