In today’s digital banking environment, fraud doesn’t announce itself. It operates in the shadows—milliseconds between a legitimate transaction and a sophisticated attack that drains accounts, damages reputations, and triggers regulation accuracy.
For Saudi financial institutions navigating rapid digital transformation, the challenge is clear: traditional fraud detection methods are no longer enough. Rule-based systems that once served as the backbone of fraud prevention now struggle against adaptive attackers who evolve faster than static rules can follow.
This is where real-time fraud detection solutions powered by behavioral intelligence are transforming the security landscape—giving banks, fintechs, and payment providers the ability to see what their backend systems simply cannot.
Why Fraud Is Growing Faster Than Saudi Banks Can Respond
Saudi Arabia’s Vision 2030 has accelerated digital transformation across the financial sector. Mobile banking adoption has surged, digital payment volumes have multiplied, and fintech innovation is reshaping how millions of Saudis interact with their money.
But with opportunity comes risk:
- Account takeover attacks have increased significantly across GCC banking platforms
- Synthetic identity fraud is becoming more sophisticated and harder to detect
- Real-time payment systems create new attack vectors that legacy systems weren’t designed to handle
- SAMA’s cybersecurity framework now demands proactive fraud prevention, not just reactive response
The regulatory landscape is equally demanding. SAMA’s Cyber Security Framework and the Personal Data Protection Law (PDPL) require financial institutions to demonstrate robust fraud prevention capabilities—capabilities that traditional detection methods often cannot provide.
What’s Wrong with Traditional Fraud Detection?
Most legacy fraud detection systems operate on a simple principle: define rules, match patterns, flag anomalies. While this approach caught obvious fraud in the past, today’s attackers have learned to operate within these rules.
The limitations are significant:
Rule-based systems generate excessive false positives. When 90% of flagged transactions turn out to be legitimate, investigation teams become overwhelmed, and real threats slip through the noise.
Static rules cannot adapt to new attack patterns. By the time a rule is written to catch yesterday’s fraud, attackers have already moved on.
Batch processing creates detection delays. In a world where transactions complete in seconds, reviewing fraud alerts hours or days later is simply too late.
For organizations serious about fraud prevention, the path forward requires a fundamentally different approach—one built on real-time behavioral intelligence.
How Real-Time Fraud Detection Solutions Work
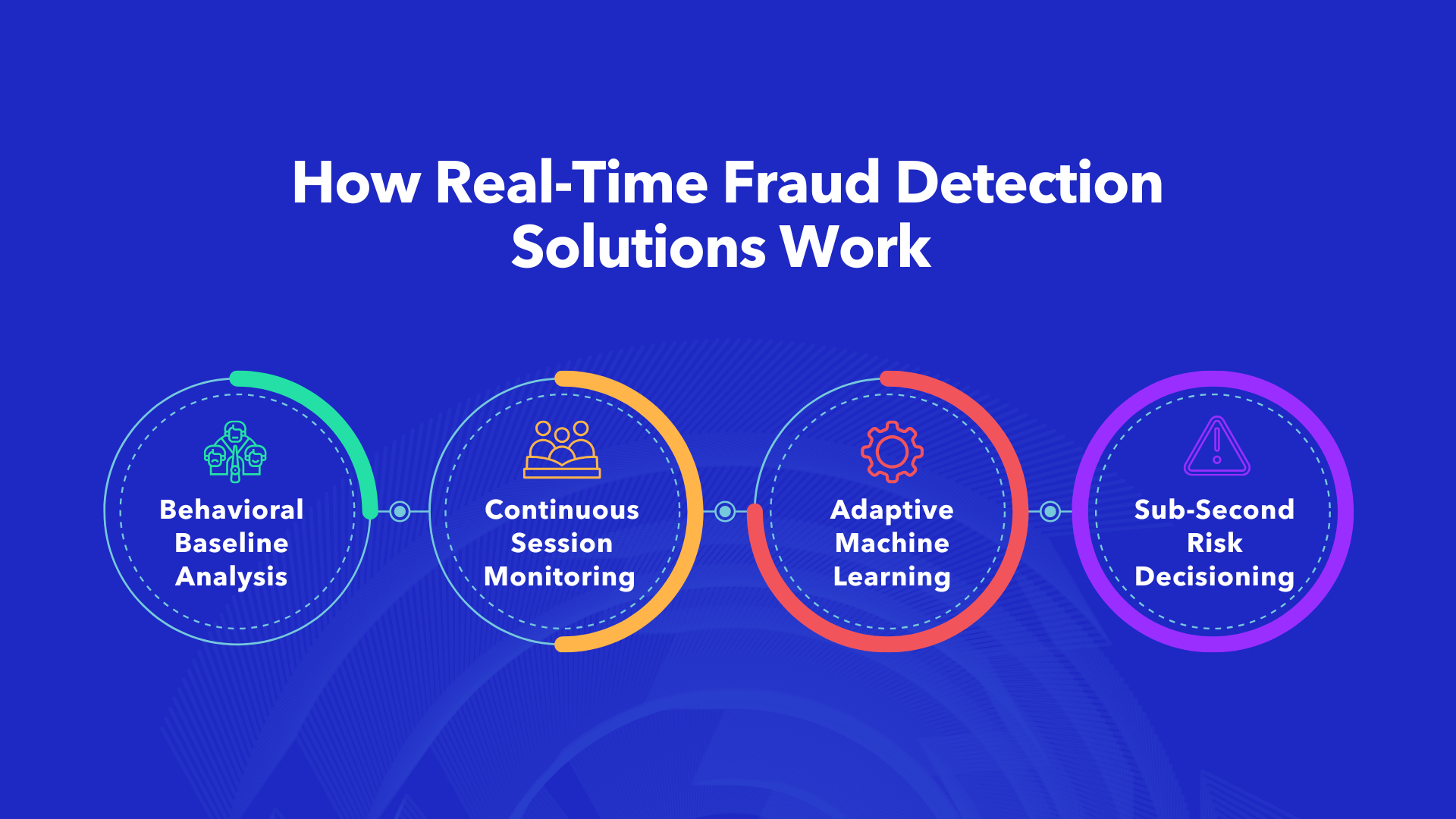
Real-time fraud detection solutions work differently. Instead of matching transactions against static rules, they analyze behavioral signals across every interaction—building dynamic risk profiles that evolve with each user session.
Behavioral Baseline Analysis
The system learns what “normal” looks like for each user—their typical transaction patterns, device preferences, geographic behaviors, and interaction rhythms. When behavior deviates from this baseline, risk scores adjust automatically.
Continuous Session Monitoring
Rather than evaluating transactions in isolation, real-time fraud detection solutions monitor entire sessions—identifying suspicious patterns like rapid navigation changes, unusual data entry behaviors, or session anomalies that signal potential account takeover.
Adaptive Machine Learning
Unlike static rules, ML-powered detection continuously learns from new data. When attackers adapt their methods, the system adapts its detection—without requiring manual rule updates.
Sub-Second Risk Decisioning
Risk assessments happen in milliseconds, enabling organizations to block fraudulent transactions before they complete rather than investigating after the damage is done.
Key Capabilities of Real-Time Fraud Detection Solutions for Saudi Banks
For Saudi financial institutions evaluating real-time fraud detection solutions, several capabilities are essential:
1. Transaction Risk Scoring
Every transaction receives a dynamic risk score based on multiple behavioral and contextual signals. High-risk transactions can be blocked, stepped up for additional authentication, or flagged for review—all in real-time.
2. Device and Session Intelligence
Understanding the device and session context is critical. Real-time fraud detection solutions analyze device fingerprints, session behaviors, and environmental signals to identify compromised accounts or fraudulent access attempts.
3. Identity Verification Integration
Modern fraud detection doesn’t operate in isolation. Integration with identity verification workflows ensures that suspicious sessions trigger appropriate authentication challenges without disrupting legitimate users.
4. SAMA-Aligned Reporting
Regulatory compliance requires comprehensive audit trails and reporting capabilities. Real-time fraud detection solutions provide the documentation needed to demonstrate compliance with SAMA’s cybersecurity framework and fraud prevention requirements.
The Business Case: Why Real-Time Detection Pays Off
Fraud prevention has traditionally been viewed as a cost center—a necessary expense to minimize losses. Real-time fraud detection solutions change this equation:
- Reduced False Positive Rates: Organizations typically see 50-70% reductions in false positives, freeing investigation teams to focus on genuine threats.
- Lower Fraud Losses: Real-time detection stops fraud before completion, dramatically reducing direct financial losses.
- Improved Customer Experience: By reducing friction for legitimate users while stopping fraudsters, organizations protect both their assets and their customer relationships.
- Regulatory Confidence: Demonstrating proactive fraud prevention capabilities strengthens relationships with regulators and reduces compliance risk.
Leading Saudi financial institutions are already recognizing that real-time fraud detection represents not just a security investment, but a competitive advantage.
How to Implement Real-Time Fraud Detection Successfully
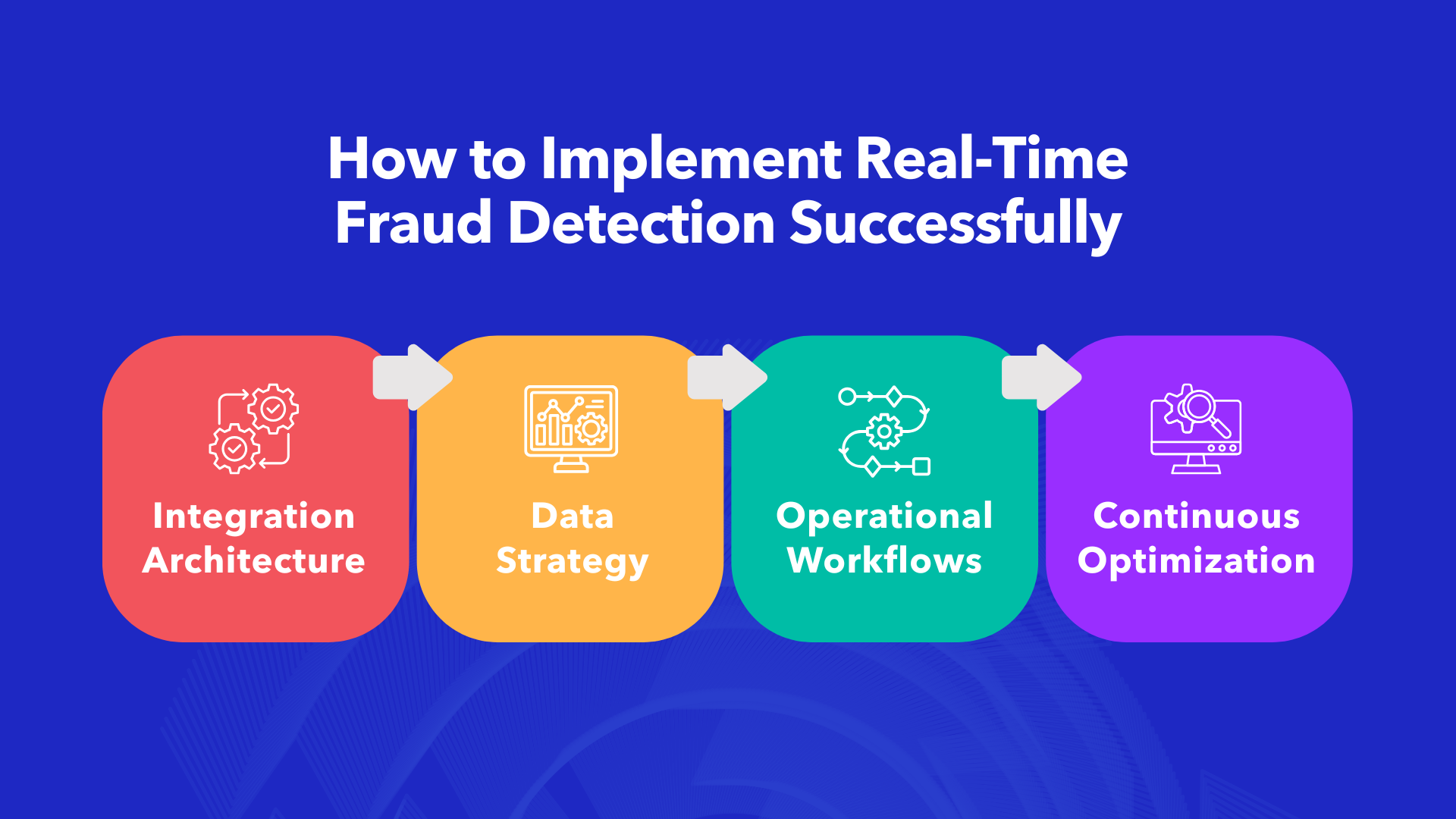
For organizations ready to move beyond traditional fraud detection, several factors will determine success:
Integration Architecture: Real-time fraud detection solutions must integrate seamlessly with existing banking systems, payment gateways, and authentication workflows.
Data Strategy: Effective behavioral intelligence requires access to the right data signals—transaction data, session information, device context, and historical patterns.
Operational Workflows: Detection is only valuable if organizations can act on insights. Clear escalation procedures and response workflows are essential.
Continuous Optimization: Fraud patterns evolve constantly. Regular model tuning and threshold optimization ensure detection remains effective over time.
Conclusion: Why Real-Time Fraud Detection Solutions Are No Longer Optional
The fraud landscape will continue to evolve. Attackers will develop new techniques, exploit new vulnerabilities, and target organizations that haven’t adapted their defenses.
For Saudi financial institutions committed to protecting their customers, their assets, and their regulatory standing, real-time fraud detection solutions powered by behavioral intelligence offer a clear path forward—transforming fraud prevention from a reactive burden into a proactive strategic advantage.
Fraud will target your organization—that’s inevitable. What matters is whether you detect it before or after the damage is done.
If your current systems aren’t giving you real-time visibility, it’s time to rethink your approach.
